Don't compromise on security in your practice. Help your staff better identify risks and mitigate potential impacts of data breaches and cyber-attacks.
How many of us have, at one time or another, needed to run down to the shops to pick up a bottle of milk or loaf of bread, and told ourselves that we don’t need to wear a seatbelt because it’s only a 30-second trip?
Often, the arguments we use to justify our decisions in situations such as these centre around the premise of, ‘the bad thing won’t happen to me.’
Optimism bias is the mistaken belief that our chances of experiencing positive events are greater, and undesirable events are lower when compared to that of our peers. While a pleasant thought, optimism bias exposes us to uninformed, and often risky decision-making.
When it comes to cyber-security and implementing proper processes, it’s all too easy to lump it into the ‘too hard’ basket. After all, with billions of people and millions of organisations around the world interacting with these online systems, what are the chances that you will be chosen as a target?
With recent widespread and well-publicised cyber-attacks against Optus and Medibank, there is no better time to review your practice’s security processes.
You are an Attractive Target
Health service providers are an attractive target for hackers and cyber-criminals.
Day-to-day operations of a practice will necessitate the collection and storage of vast swathes of sensitive patient data; not only names, addresses and contact details, but Medicare information, identifying documentation, and payment details.
In the Office of the Australian Information Commissioner’s Notifiable Data Breaches Report for the period of July to December 2021, Health Service Providers were by far the most affected industry sector to notify data breaches, with Finance and Legal, Accounting and Management Services coming in second and third, respectively.
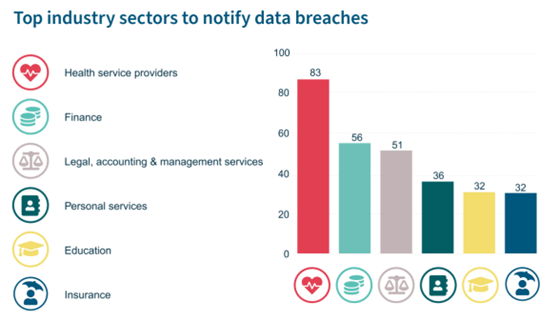
Consider how valuable health provider data must be, if they were preferred targets over financial institutions, those who handle large amounts of money!
With that in mind, it’s worth taking a moment to consider the processes your practice has in place. While it is incredibly difficult to eliminate risk altogether, there are steps that can be taken to ensure that the risk to your practice and its data is kept to a minimum.
Often, this can be as simple as making sure your practice staff are properly trained in how to react in situations when something doesn’t look or feel right.
How Dangerous Can Cyber Attacks Be?
In September 2013, Target America was the victim of a cyber-attack that saw the personal and financial information of more than 100 million customers compromised. In strictly financial terms, Target has had to spend more than USD$200 million across settlement claims, class action suits, compensation fees, legal fees, insurance, and more – not to mention untold reputational damage.
Surely a cyber-attack of this scale and severity would have been a highly organised, meticulously planned, nigh-unpreventable assault on Target’s security, right?
The answer might surprise you.
No matter how secure you believe your systems may be, you’re only as strong as your weakest link. In Target’s case, they had contracted a mechanics agency to look after refrigeration in some of their stores. As such, this agency had login details to Target’s systems.
Hackers sent phishing emails to third parties – malicious emails which were designed to look like they originated from legitimate organisations. One of the staff members from the mechanics agency clicked a link in one of these emails, and from there, the floodgates opened.
Using credentials that were stolen from the agency’s system, hackers infiltrated Target America’s IT system, and then navigated their way to data on their POS terminals. From there, they covertly installed malware that collected data each time a customer paid with a credit card. They then transferred this data to a holding file in a less secure area of Target’s IT system and continued to collect data – undetected – for two weeks. One week before Christmas 2013, nearly 11 gigabytes of credit card information and customer data were transferred to a server in Russia.
By the time Target realised what was going on – it was far too late. The damage had been done.
A New Type of Hacker
When many of us hear the word hacker, we think of a hooded figure hunched over a keyboard with half a dozen screens streaming code that would look at home in a Matrix film. We think of phrases from movies like ‘infiltrating the mainframe’ and ‘bypassing the firewall’.
Those kinds of brute-force attacks, while they do exist, are far less prevalent than simple social engineering. Why ‘hack’ your way to someone’s personal details painstakingly and forcibly when you can get them to offer them on a silver platter, simply by asking the right questions?
Have you ever been on Facebook and stumbled across an innocent-looking quiz that asks for your mother’s maiden name and the name of the street you grew up to generate your unique superhero name? It seems like harmless fun, but the answers to those two questions are commonly used as security passwords for sensitive information.
Posts like these often see incredibly high levels of engagement, and without realising it, users are manipulated into giving away details which could ultimately lead to their accounts (both on Facebook and elsewhere) being compromised.
In the context of a medical practice, social engineering is a tool that is often utilised to gain access to sensitive patient information, your practice database, swathes of financial information, and much more.
Often, these attempts on your data won’t be secretive, or subtle, and they won’t come from a shadowy figure hiding behind computer screens. They might come from:
- A ‘patient’ who needs to change their details, but forgot to bring ID
- A salesperson offering a product or service to improve your practice operations, and all you need to do is download a program from a link they’ll send you
- A technician who has been sent on behalf of your regular IT provider and needs to do some maintenance on your network, or
- A smiling stranger who gets access to your staff break room by name-dropping your practice owner or manager
Attempts like these can occur right in front of you, and in the middle of a busy day. You may not think twice about changing someone’s details, clicking on a link, or granting someone access to your network.
Be Alert, Not Alarmed
It’s easy to hear all of this and immediately go into panic mode. Relax!
With a little bit of training and implementation of proper cyber-security processes, you can work to effectively minimise risk to your practice and its data.
Train staff to be alert and cautious
Your practice staff is almost guaranteed to be the point of contact at which your practice security is tested. Ensure that they are aware of common methods that might be used to compromise your practice data.
Rollout sensible restrictions
Conduct regular audits of staff permissions to review whether they need access to all the data available to them. Consider which data should be accessible by whom.
Protect your credentials
Usernames and passwords are the proverbial keys to the kingdom. Under no circumstances should they be written down on post-it notes and stuck to a monitor! If your team has trouble remembering login credentials, encourage using a secure password manager.
Increase physical security
Consider implementing measures such as swipe cards or access codes for areas of your practice that house sensitive data or hardware.
Trust your IT professionals
If you receive an email prompting you to click on a link, or someone is asking you to install a program handed to you on a USB drive, and something doesn’t feel right, consult your IT team. They’ll be able to verify whether the request is genuine and, if not, how to proceed safely.
Hold every department accountable for security
As we saw with the Target data breach, poor security practices from anyone involved with your business can lead to compromised data. Make sure that anyone accessing your practice’s systems knows your security protocols and expectations.
But It Won’t Happen to Me…
It’s easy to lull yourself into a false sense of security when considering the kind of organisations that suffer widely publicised cyber-attacks. They’re often large, well-known corporations that are worth billions of dollars. It’s not hard to understand why they’d be prime targets.
But the complacency which enables this mentality is exactly why your medical practice is not immune from attempted data breaches. Furthermore, while your practice data may not be as valuable in a purely fiscal sense, your patients’ data deserves just as much respect regarding privacy and security.
Don’t fall into the trap of compromising your cyber-security. It simply isn’t worth the risk.
Authored by:
Louis Valenti
Marketing & Communications Leader at Best Practice Software
Explore our range of news and training resources:
Bp Learning Video Library | Bp Learning Training Options | Bp Newsroom Blog
Subscribe to Our Newsletters | Bp Learning Webinars

